 By: John Abhilash / April 3, 2024
By: John Abhilash / April 3, 2024
Demystifying the Cloud: Your Essential Guide to Cloud Access Security Brokers (CASBs)
The cloud revolution has fundamentally transformed how businesses operate. From data storage and software applications to entire IT infrastructures, the cloud offers unparalleled scalability, agility, and cost-effectiveness. However, this shift to cloud-based resources introduces new security challenges. Traditional security perimeters built around physical data centers no longer exist in the cloud environment. This creates blind spots and exposes sensitive data to potential threats.
Cloud Access Security Brokers (CASBs) emerge as the gatekeepers of this new frontier. They act as a comprehensive security solution designed to navigate the ever-evolving cloud landscape. CASBs function as an intelligent security policy enforcement layer situated between your organization and the vast array of cloud services it utilizes. They offer a multi-faceted approach to cloud security, encompassing:
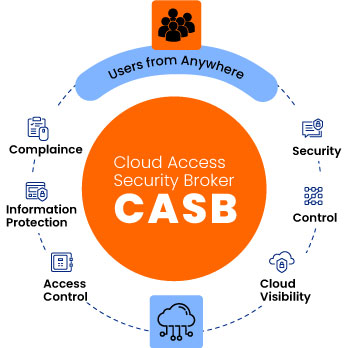
1.Visibility into the Shadow IT Landscape: Many employees unknowingly leverage unauthorized cloud applications (shadow IT). CASBs provide unparalleled visibility into these applications, enabling you to assess their security posture and take appropriate action. This can involve integrating these applications into the sanctioned cloud environment, disabling them if deemed too risky, or educating employees about secure cloud usage practices.
2.Fortifying Data Security: Cloud storage introduces inherent data security risks. CASBs go beyond basic access control by offering robust Data Loss Prevention (DLP) capabilities. DLP features prevent sensitive information from leaking accidentally or intentionally, whether through unauthorized downloads, uploads, or cloud misconfigurations. CASBs can also encrypt data at rest and in transit, adding an extra layer of protection.
While CASBs simplify compliance with industry-specific regulations like HIPAA, PCI DSS, and GDPR by demonstrating adherence to specific data security and privacy controls, their benefits extend far beyond regulatory mandates.

1.Proactive Threat Detection and Prevention: Cyberattacks are constantly evolving, and traditional security solutions often struggle to keep pace. CASBs leverage advanced analytics and threat intelligence to identify and block sophisticated threats like malware, phishing attempts, and zero-day exploits targeting your cloud environment. They can also monitor user behavior within cloud applications and identify deviations from normal patterns, potentially revealing insider threats or compromised accounts.
2.Cloud Application Security (CASB): Some CASBs integrate Cloud Application Security features that scan cloud applications for vulnerabilities and misconfigurations. This proactive approach helps identify and address security weaknesses before they can be exploited by attackers.
3.API Security Management: As APIs become the cornerstone of modern cloud applications, CASBs with API security management capabilities can secure API communication channels and prevent unauthorized access to sensitive data. This is crucial as poorly secured APIs can be a gateway for attackers to breach your cloud environment.
Leading CASB solutions offer a range of advanced functionalities:
1.User and Entity Behavior Analytics (UEBA): CASBs equipped with UEBA capabilities can analyze user activity data from various sources, including cloud applications, emails, and network logs. This allows for the identification of suspicious behavior patterns that might indicate potential security incidents.
2.Secure Web Gateways (SWGs): Some CASBs integrate SWG functionality, which filters web traffic to prevent access to malicious websites or phishing attempts. This adds an extra layer of protection for users accessing the internet through cloud applications.
3.Cloud Workload Protection Platform (CWPP): A few CASBs offer CWPP capabilities, which provide security for workloads running in the cloud environment. This includes features like vulnerability scanning, intrusion detection, and workload activity monitoring.
Selecting the ideal CASB solution requires careful consideration of your organization’s unique needs. Here are some key factors to evaluate:
1.Security Feature Alignment: Assess the CASB’s ability to address your specific security concerns. Prioritize features based on your industry compliance requirements, data sensitivity levels, and desired level of threat detection and prevention. Focus on features that align with your organization’s security posture and future security goals.
2.Deployment Model Flexibility: CASBs are available in various deployment models, including:
2a)Cloud-Based CASBs: Offered as a managed service, cloud-based CASBs are easy to deploy and require minimal IT resources. However, they may offer less control over data security compared to on-premise solutions.
2b)On-Premise CASBs: Provide greater control over data security but require more significant upfront investment and ongoing maintenance. They may also be less scalable than cloud-based solutions.
2c)Hybrid CASBs: Combine the flexibility of a cloud-based solution with the control of an on-premise deployment. This option allows for a more customized security approach.
The convergence of CASBs with SASE principles is a significant trend shaping the future of cloud security. SASE emphasizes context-aware access control, where access decisions are based on a user’s identity, device, location, application, and real-time threat intelligence. CASBs play a vital role in SASE architectures by enforcing security policies at the cloud access layer. This integrated approach provides a comprehensive and dynamic security posture for cloud environments.
Furthermore, the Zero Trust security model, which assumes no user or device is inherently trustworthy, is gaining traction. CASBs align perfectly with Zero Trust principles by continuously verifying user access, enforcing granular access controls (e.g., least privilege), and preventing unauthorized activity across all cloud resources. This layered approach significantly reduces the attack surface and minimizes the potential impact of security breaches.
Implementing a CASB is just the first step. Here are some additional considerations to maximize the value of your CASB investment:
1.User Training and Adoption: Invest in user training programs to educate employees about secure cloud usage practices and how CASBs contribute to overall data security. This can help minimize risky behavior and ensure user buy-in for the CASB solution.
2.Continuous Monitoring and Threat Intelligence: Regularly monitor CASB logs and reports to identify suspicious activity and adapt to evolving threat landscapes. Leverage threat intelligence feeds from reputable sources to stay updated on the latest cyber threats and adjust your security posture accordingly.
3.Integration with Security Ecosystem: Ensure your CASB integrates seamlessly with your existing security tools like firewalls, intrusion detection systems (IDS), and security information and event management (SIEM) solutions. This integrated approach allows for a holistic view of your security posture and facilitates efficient incident response.
In today’s cloud-powered world, CASBs have become an essential security tool. They empower organizations to leverage the immense benefits of cloud computing while mitigating associated security risks. By providing comprehensive visibility, granular access control, robust data security measures, and advanced threat detection capabilities, CASBs ensure a secure and compliant cloud environment.
By carefully selecting a CASB solution that aligns with your specific needs, implementing best practices like user training and continuous monitoring, and staying abreast of evolving security trends, organizations can confidently embrace the cloud journey, knowing their data and applications are protected against the ever-evolving threat landscape. CASBs are the gatekeepers of your cloud security, and with the right approach, they can unlock the full potential of cloud computing while keeping your data safe.
Guardian: Revolutionizing Application Security
Key Features of Guardian:
1.Shift Left Security : Early Vulnerability Detection
2.Fast Track your VAPT: Gain insights to your application security posture across various assessments (SCA, SAST, DAST, IAC)
3.Security Driven Development : Streamlined Vulnerability Assessment and Penetration Testing(VAPT)
4.Integration with JIRA: Provided a centralized hub for tracking ,prioritizing and managing security issues.
5.AI powered Remediations: Immediate Resolution Guidance
Guardian’s AI delivers immediate resolution guidance upon identifying vulnerabilities, accelerating the remediation process and fostering a culture of proactive security to enhance overall code quality.
In an era where cybersecurity is paramount, Guardian serves as an indispensable ally, safeguarding applications throughout their lifecycle and empowering businesses to navigate the digital landscape with confidence.
Check Out our Other Resources: CASB vs SASE / OpenTofu Vs Terraform Title: Demystifying the Cloud: Your Essential Guide to Cloud Access Security Brokers (CASB)

Leave a Comment