 By: John Abhilash / March 4, 2024
By: John Abhilash / March 4, 2024
Unlocking the Key to Secure Cloud Access with Cloud Access Security Brokers (CASBs)
In today’s digital landscape, cloud adoption is skyrocketing. Businesses of all sizes are migrating to the cloud to leverage its scalability, cost-effectiveness, and agility. However, this shift presents a new set of security challenges. Traditional security solutions designed for on-premises environments struggle to adapt to the dynamic and distributed nature of the cloud. This is where Cloud Access Security Brokers (CASBs) come in, acting as the key to unlocking secure cloud access.
A CASB is a security software solution that acts as an intermediary between your organization and the various cloud services you utilize. It sits between your users and cloud applications, monitoring all activity and enforcing your organization’s security policies. Essentially, a CASB acts as a security checkpoint for your cloud environment.
As businesses move their data and applications to the cloud, they lose a significant degree of control. Cloud service providers (CSPs) are responsible for the security of their infrastructure, but the responsibility for securing your data within the cloud ultimately rests with your organization. This is where CASBs play a crucial role:
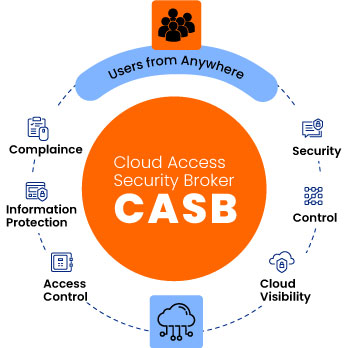
1. Enhanced Visibility and Control: CASBs provide comprehensive visibility into your cloud environment, allowing you to:
i)Identify and monitor all cloud applications used by employees, including sanctioned and unsanctioned (“shadow IT”) applications.
ii)Gain insights into user activity within cloud applications to identify potential risks and suspicious behavior.
iii)Enforce granular access controls to ensure only authorized users have access to specific data and functionalities within cloud applications.
2. Data Protection and Threat Prevention: CASBs offer robust data security features to safeguard your sensitive information in the cloud:
i)Data Loss Prevention (DLP): CASBs can prevent sensitive data from being exfiltrated from your cloud environment, whether through intentional or accidental means.
ii)Data Encryption: CASBs can encrypt data at rest and in transit, adding an extra layer of security to your cloud data.
iii)Threat Detection and Prevention: CASBs can scan cloud applications for malware, phishing attempts, and other security threats.
3. Regulatory Compliance: CASBs can help your organization meet various industry regulations and data privacy laws, such as:
CASBs can automate compliance tasks, such as data classification and activity logging, making it easier for your organization to demonstrate adherence to regulatory requirements.
4. Improved User Experience: CASBs can streamline the cloud access experience for your users by:
i)Providing single sign-on (SSO) capabilities: Users can access all authorized cloud applications with a single set of credentials, enhancing convenience and security.
ii)Automating access provisioning and deprovisioning: CASBs automate the process of granting and revoking access to cloud applications based on user roles and permissions, saving time and effort for IT administrators.
Key Features and Capabilities of CASBs
The specific features and capabilities of a CASB can vary depending on the vendor, but some common functionalities include:
i)Cloud application discovery and inventory: Identifying and cataloging all cloud applications being used within the organization.
ii)User and access control: Managing user identities, roles, and permissions for accessing cloud applications.
iii)Data security: Implementing DLP, data encryption, and activity monitoring measures to protect sensitive data.
iv)API security: Securing APIs used to access and manage cloud resources to prevent unauthorized access or data breaches.
iv)Threat detection and prevention: Identifying and blocking malware, phishing attacks, and other security threats to safeguard cloud infrastructure and data.
vi)Compliance management: Streamlining compliance tasks and reporting to ensure adherence to industry regulations and internal policies.
vii)Analytics and reporting: Providing insights into cloud activity, user behavior, and potential security risks through comprehensive analytics and reporting tools.
With a multitude of CASB vendors offering diverse solutions, selecting the right one for your organization can be overwhelming. Here are some key factors to consider:
i)Your organization’s specific security needs and requirements.
ii)The types of cloud services you use (SaaS, PaaS, IaaS).
iii)The size and complexity of your IT environment.
iv)Your budget and deployment preferences (cloud-based, on-premises, or hybrid).
v)t’s crucial to evaluate different CASB solutions and conduct thorough due diligence before making a decision.
By embracing CASBs and staying informed about the latest advancements, organizations can unlock the full potential of the cloud while ensuring the security and compliance of their data and applications.
Cloud adoption is undeniable, but secure access is paramount. Cloud Access Security Brokers (CASBs) are essential tools for organizations to:
i)Gain visibility and control over their cloud environment.
ii)Protect sensitive data from unauthorized access and exfiltration.
iii)Comply with industry regulations and data privacy laws.
iv)Improve the user experience for cloud access.
As cloud security continues to evolve, CASBs will remain at the forefront, providing organizations with the key to unlocking secure cloud access in the years to come.
Guardian: Revolutionizing Application Security
Key Features of Guardian:
1.Shift Left Security : Early Vulnerability Detection
2.Fast Track your VAPT: Gain insights to your application security posture across various assessments (SCA, SAST, DAST, IAC)
3.Security Driven Development : Streamlined Vulnerability Assessment and Penetration Testing(VAPT)
4.Integration with JIRA: Provided a centralized hub for tracking ,prioritizing and managing security issues.
5.AI powered Remediations: Immediate Resolution Guidance
Guardian’s AI delivers immediate resolution guidance upon identifying vulnerabilities, accelerating the remediation process and fostering a culture of proactive security to enhance overall code quality.
In an era where cybersecurity is paramount, Guardian serves as an indispensable ally, safeguarding applications throughout their lifecycle and empowering businesses to navigate the digital landscape with confidence.
Check Out our Other Resources: CASB vs SASE / OpenTofu Vs Terraform

Leave a Comment